In December 2021 – as much of the world was starting to wind down for the holidays – security researchers published details of a newly discovered vulnerability in Zoho ManageEngine.
ManageEngine is IT management software that, according to the company, has 40,000 customers worldwide, including approximately three out of every five Fortune 500 companies – thereby making a vulnerability potentially extremely dangerous.
The vulnerability, CVE-2021-40539, existed in Zoho’s ManageEngine Desktop and Desktop Central MSP. It meant that a remote attacker could use it to seize control of affected systems.
The threat has reportedly been used as part of a cyberespionage campaign to target at least nine worldwide organizations – including ones in the tech, defense, energy, healthcare, and education sectors. It’s an example of advanced persistent threat (APT) teams utilizing what are referred to as a web shell.
What is a web shell?
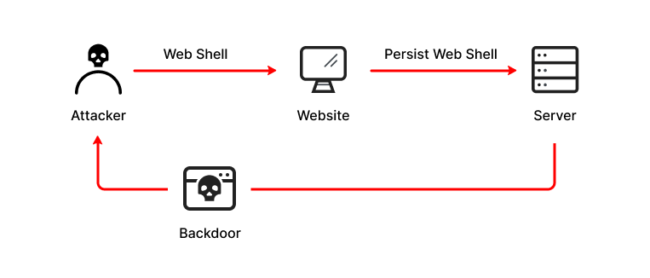
A web shell is a malicious script written in common web application languages, such as PHP and ASP. They let attackers compromise web servers, as well as launching additional attacks. That could include anything from exfiltrating data to uploading malware. These attacks start with the bad actors penetrating a network or system, and then installing the web shell to gain a foothold that they can use to access the target networks. After this, they can then utilize it as a backdoor to target specific web applications as well as connected systems.
Web shell attacks are popular (with attackers; certainly not with legitimate users) because executing an attack can be carried out using the HTTP protocol found in web browsers, and do not require extra programs. The small pieces of code needed to launch a web shell attack can simply be dropped onto a web server, and are incredibly tough to detect.
That means that attackers can use them to access compromised systems for long periods of time.
Web shell attacks are on the rise
This is far from the first example of attackers using web shells as part of an attack. For example, in 2018 and 2019 a hacker group called GALLIUM attacked various telecommunications providers with web shells to target internet-facing services. Another group using web shells is the Lazarus group, linked to the government of North Korea. According to research carried out by Microsoft, web shell-based attacks have increased to upward of 140,000 incidents per month.
Responding to attacks such as these, the FBI later managed to clear malicious web shells from many vulnerable computers located in the United States. These were compromised with a commonly known Proxy Logon Microsoft Exchange vulnerability.
However, the problem continues to persist due to web shell attack’s combination of low barrier to entry (making them easy to deploy) and difficulty in detection (making them hard to discover.)
Protecting against web shell attacks
Protecting against malicious web shells is essential. One way to do this is to ensure that privilege is fully considered when granting the necessary permissions for use in web applications. Using the least privilege concept (meaning giving users the minimum level of access that they need in order to do their job) means that accounts which are compromised cannot cause as much damage due to in-built restrictions.
Other proactive steps include the proactive patching of internet-facing vulnerabilities when they’re discovered, as well as strong network segmentation strategies to avoid ingrained network intrusions in the event of server compromises. In addition, organizations should make sure that they review and audit web server logs regularly, and also check perimeter firewalls and proxies so as to restrict unneeded services access.
There are also various cyber security solutions that organizations can avail themselves of. For example, file integrity monitoring (FIM) tools can assist by detecting and blocking file changes related to web directories. By spotting issues quickly, security employees can be alerted of web shells so that they can rapidly find them and remove them.
Other solutions include intrusion prevention systems (IPS), which monitor network traffic flow to protect IT environments, web application firewalls (WAF), which monitor, filter and block HTTP traffic, Runtime Application Self-Protection (RASP), API security, and more. By deploying solutions such as this, organizations can defend against web shells (and plenty more attacks, to boot.)
Businesses which do not have such tools in place should make sure that they seek out the proper recommendations from the right cyber security experts.
Web shell attacks will continue
Incidents such as the Zoho ManageEngine web shell attack will continue to happen. As noted above, the “selling point” for attackers when it comes to web shells makes them a compelling mode of attack on targets.
It’s crucial that businesses do what they can to protect themselves against such attacks. By utilizing the right techniques it’s possible to safeguard against these instances. Doing so is absolutely the right thing for all involved.